Preparing for Manual Windscribe Setup
Verify your Windscribe login information
If you are not already an Windscribe user Sign Up Now.
1. Log in to your account on the Windscribe website.
2. Click on the Download link at the top of the page.
3. Scroll down to the Config Generators section and Click on the OpenVPN link.
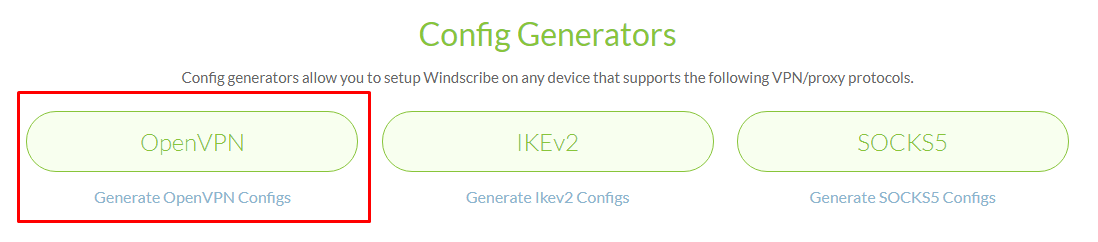
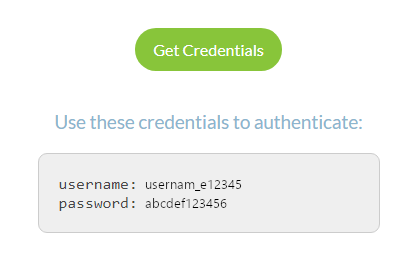
4. Click on Get Credentials and copy the Username and Password. This information will be used later on in the configuration.
Windscribe Server Addresses
United States
US East:
us-east.windscribe.com
US West:
us-west.windscribe.com
US Windflix:
wf-us.windscribe.com
Canada
Canada:
ca.windscribe.com
Canada West:
ca-west.windscribe.com
Additional Servers
Australia:
au.windscribe.com
Austria:
at.windscribe.com
Belgium:
be.windscribe.com
Brazil:
br.windscribe.com
Bulgaria:
bg.windscribe.com
Czech Republic:
cz.windscribe.com
Denmark:
dk.windscribe.com
Egypt:
eg.windscribe.com
Finland:
fi.windscribe.com
France:
fr.windscribe.com
Germany:
de.windscribe.com
Hong Kong:
hk.windscribe.com
Hungary:
hu.windscribe.com
India:
in.windscribe.com
Ireland:
ie.windscribe.com
Italy:
it.windscribe.com
Japan:
jp.windscribe.com
Latvia:
lv.windscribe.com
Luxemburg:
lu.windscribe.com
Malaysia:
my.windscribe.com
Mexico:
mx.windscribe.com
Netherlands:
nl.windscribe.com
Norway:
no.windscribe.com
Poland:
pl.windscribe.com
Romania:
ro.windscribe.com
Russia:
ru.windscribe.com
Singapore:
ch.windscribe.com
South Africa:
za.windscribe.com
South Korea:
kr.windscribe.com
Spain:
es.windscribe.com
Sweden:
se.windscribe.com
Switzerland:
ch.windscribe.com
Taiwan:
tw.windscribe.com
Turkey:
tr.windscribe.com
Ukraine:
ua.windscribe.com
United Kingdom:
uk.windscribe.com
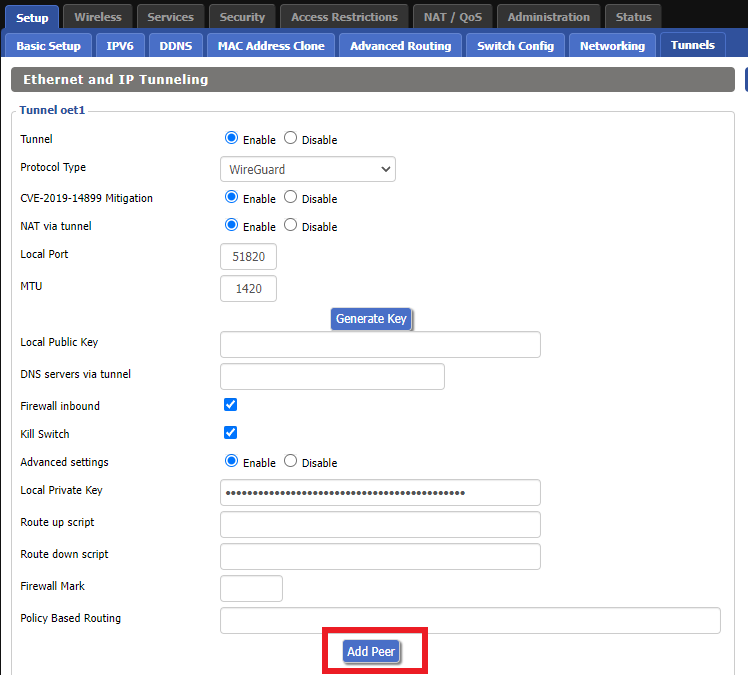
DD-WRT Router Setup for Windscribe
Navigate to Services > VPN
Enter Windscribe settings
OpenVPN Client
Start OpenVPN Client
If you wish to disable your VPN connection simply set this to Disable at any time and click Apply Settings.
Server IP/Name
Copy and Paste the server you would like to connect to from the server list above. Be sure there are no extra spaces or characters.
If you wish to change Windscribe connection locations, THIS IS THE ONLY FIELD YOU NEED TO CHANGE.
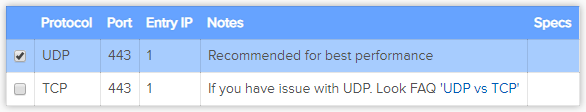
Port
443
Tunnel Device
TUN
Tunnel Protocol
UDP
Encryption cipher
AES-256-CBC
Hash Algorithm
SHA512
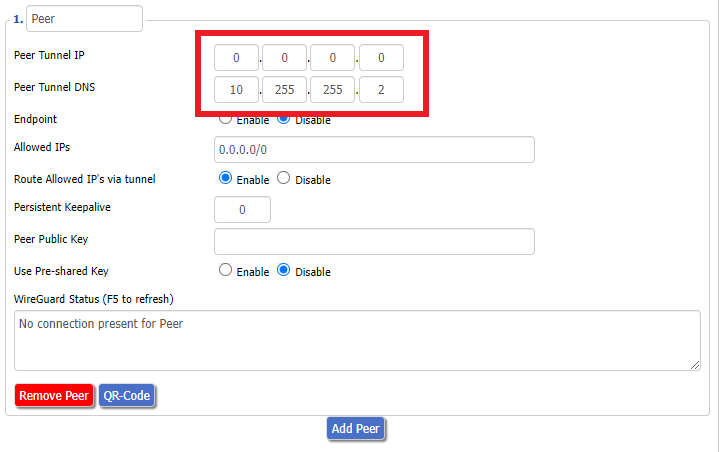
User Pass Authentication
Enable
Username
Enter your OpenVPN specific Username.
Password
Enter your OpenVPN specific Password.
Advanced Options
Enable
TLS Cipher
None
LZO Compression
Adaptive
NAT
Enable
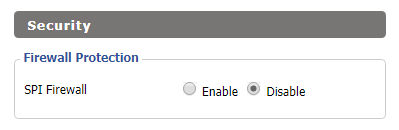
Firewall Protection
Enable
TLS Auth Key
-----BEGIN OpenVPN Static key V1----- 5801926a57ac2ce27e3dfd1dd6ef8204 2d82bd4f3f0021296f57734f6f1ea714 a6623845541c4b0c3dea0a050fe6746c b66dfab14cda27e5ae09d7c155aa554f 399fa4a863f0e8c1af787e5c602a801d 3a2ec41e395a978d56729457fe6102d7 d9e9119aa83643210b33c678f9d4109e 3154ac9c759e490cb309b319cf708cae 83ddadc3060a7a26564d1a24411cd552 fe6620ea16b755697a4fc5e6e9d0cfc0 c5c4a1874685429046a424c026db672e 4c2c492898052ba59128d46200b40f88 0027a8b6610a4d559bdc9346d33a0a6b 08e75c7fd43192b162bfd0aef0c716b3 1584827693f676f9a5047123466f0654 eade34972586b31c6ce7e395f4b478cb -----END OpenVPN Static key V1-----
Additional Config
tun-mtu-extra 32
mssfix 1450
persist-key
persist-tun
Policy Based Routing
This field can be used for split VPN and Dual Gateway routing.
CA Cert
-----BEGIN CERTIFICATE----- MIIFozCCA4ugAwIBAgIBATANBgkqhkiG9w0BAQ0FADBAMQswCQYDVQQGEwJDSDEV MBMGA1UEChMMUHJvdG9uVlBOIEFHMRowGAYDVQQDExFQcm90b25WUE4gUm9vdCBD QTAeFw0xNzAyMTUxNDM4MDBaFw0yNzAyMTUxNDM4MDBaMEAxCzAJBgNVBAYTAkNI MRUwEwYDVQQKEwxQcm90b25WUE4gQUcxGjAYBgNVBAMTEVByb3RvblZQTiBSb290 IENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAt+BsSsZg7+AuqTq7 vDbPzfygtl9f8fLJqO4amsyOXlI7pquL5IsEZhpWyJIIvYybqS4s1/T7BbvHPLVE wlrq8A5DBIXcfuXrBbKoYkmpICGc2u1KYVGOZ9A+PH9z4Tr6OXFfXRnsbZToie8t 2Xjv/dZDdUDAqeW89I/mXg3k5x08m2nfGCQDm4gCanN1r5MT7ge56z0MkY3FFGCO qRwspIEUzu1ZqGSTkG1eQiOYIrdOF5cc7n2APyvBIcfvp/W3cpTOEmEBJ7/14RnX nHo0fcx61Inx/6ZxzKkW8BMdGGQF3tF6u2M0FjVN0lLH9S0ul1TgoOS56yEJ34hr JSRTqHuar3t/xdCbKFZjyXFZFNsXVvgJu34CNLrHHTGJj9jiUfFnxWQYMo9UNUd4 a3PPG1HnbG7LAjlvj5JlJ5aqO5gshdnqb9uIQeR2CdzcCJgklwRGCyDT1pm7eoiv WV19YBd81vKulLzgPavu3kRRe83yl29It2hwQ9FMs5w6ZV/X6ciTKo3etkX9nBD9 ZzJPsGQsBUy7CzO1jK4W01+u3ItmQS+1s4xtcFxdFY8o/q1zoqBlxpe5MQIWN6Qa lryiET74gMHE/S5WrPlsq/gehxsdgc6GDUXG4dk8vn6OUMa6wb5wRO3VXGEc67IY m4mDFTYiPvLaFOxtndlUWuCruKcCAwEAAaOBpzCBpDAMBgNVHRMEBTADAQH/MB0G A1UdDgQWBBSDkIaYhLVZTwyLNTetNB2qV0gkVDBoBgNVHSMEYTBfgBSDkIaYhLVZ TwyLNTetNB2qV0gkVKFEpEIwQDELMAkGA1UEBhMCQ0gxFTATBgNVBAoTDFByb3Rv blZQTiBBRzEaMBgGA1UEAxMRUHJvdG9uVlBOIFJvb3QgQ0GCAQEwCwYDVR0PBAQD AgEGMA0GCSqGSIb3DQEBDQUAA4ICAQCYr7LpvnfZXBCxVIVc2ea1fjxQ6vkTj0zM htFs3qfeXpMRf+g1NAh4vv1UIwLsczilMt87SjpJ25pZPyS3O+/VlI9ceZMvtGXd MGfXhTDp//zRoL1cbzSHee9tQlmEm1tKFxB0wfWd/inGRjZxpJCTQh8oc7CTziHZ ufS+Jkfpc4Rasr31fl7mHhJahF1j/ka/OOWmFbiHBNjzmNWPQInJm+0ygFqij5qs 51OEvubR8yh5Mdq4TNuWhFuTxpqoJ87VKaSOx/Aefca44Etwcj4gHb7LThidw/ky zysZiWjyrbfX/31RX7QanKiMk2RDtgZaWi/lMfsl5O+6E2lJ1vo4xv9pW8225B5X eAeXHCfjV/vrrCFqeCprNF6a3Tn/LX6VNy3jbeC+167QagBOaoDA01XPOx7Odhsb Gd7cJ5VkgyycZgLnT9zrChgwjx59JQosFEG1DsaAgHfpEl/N3YPJh68N7fwN41Cj zsk39v6iZdfuet/sP7oiP5/gLmA/CIPNhdIYxaojbLjFPkftVjVPn49RqwqzJJPR N8BOyb94yhQ7KO4F3IcLT/y/dsWitY0ZH4lCnAVV/v2YjWAWS3OWyC8BFx/Jmc3W DK/yPwECUcPgHIeXiRjHnJt0Zcm23O2Q3RphpU+1SO3XixsXpOVOYP6rJIXW9bMZ A1gTTlpi7A== -----END CERTIFICATE-----
CLICK APPLY SETTINGS
Leave all settings not mentioned above as their default setting.
Verify a successful VPN connection
Navigate to Status > OpenVPN
- You should now see a CONNECTED SUCCESS message.
- Visit WhatIsMyIPAddress to verify your new IP address, virtual location, and status as Protected at the top of the page.
In some cases you may notice that the location is not showing the same location as the server you have input in your router settings; this is because geo tracking tools are often tricked by VPN connections. As long as you see an IP address that is not the same as your normal Internet IP address then you are indeed connected to Windscribe VPN.
Back up your settings
Navigate to Administration > Backup
- Click the Backup button.
- A file named nvrambak.bin will be saved to your computer.
- You can load nvrambak.bin to restore your settings in the event of a reset.
How to change the Windscribe server
- Copy and paste the server IP Address from the server list above into the Server IP/Name field.
- Click Apply Settings.